Group Project Data Communication by Group 9
WHAT IS OSI MODEL
The OSI open network
reference model or the OSI Reference Model for open networks is a network
architecture model developed by the International Organization for
Standardization (ISO) in Europe in 1977. Open systems interconnection or OSI
created in the form of a conceptual framework. Even now it has become a
standard connection for a computer. Moreover, it was created to fulfil a
specific purpose.
The goal is that the
OSI model becomes a reference for each vendor or developer so that the software
and products they make have interpolated properties. This means that users do
not need to make special efforts and they can collaborate with the system or product.
In OSI itself, there
are 7 layers and each of them has its own function namely physical layer, data
link layer, network layer, transport layer, session layer, presentation layer,
and application layer.
SEVEN LAYERS OF OSI MODEL
source: https://insights.profitap.com/osi-7-layers-explained-the-easy-way
1. LAYER
1: PHYSICAL LAYER
The physical layer is
responsible for the physical cable or wireless connection between network
nodes. It defines the connector, the electrical cable or wireless technology
connecting the devices, and is responsible for transmission of the raw data,
which is simply a series of 0s and 1s, while taking care of bit rate control.
It can include
specifications such as voltages, pin layout, cabling, and radio frequencies. At
the physical layer, one might find “physical” resources such as network hubs,
cabling, repeaters, network adapters or modems. For example, the Ethernet
standard for 100BaseT cable specifies the electrical characteristics of the
twisted-pair cables, the size and shape of the connectors, the maximum length
of the cables.
The OSI model upper
layers will assign meanings to the bits transmitted at the Physical Layer. One
very important type of Physical Layer device used in networks is a Network TAP.
A Network TAP is a hardware device that is used to copy the traffic on a
network link and redirect the copy to troubleshooting and analysis tools
without interrupting traffic flow or introducing a point of failure even if the
TAP loses power.
2. LAYER
2: DATA LINK LAYER
At the data link
layer, directly connected nodes are used to perform node-to-node data transfer
where data is packaged into frames. The data link layer also corrects errors
that may have occurred at the physical layer. The data link layer encompasses
two sub-layers of its own. The first, media access control (MAC), which uses
MAC addresses to connect devices and define permissions to transmit and receive
data. The second, the logical link control (LLC), which identifies network
protocols, performs error checking and synchronizes frames.
3. LAYER
3: NETWORK LAYER
The network layer is
responsible for receiving frames from the data link layer and delivering them
to their intended destinations among based on the addresses contained inside
the frame. The network layer finds the destination by using logical addresses,
such as IP (internet protocol). At this layer, routers are a crucial component
used to quite literally route information where it needs to go between
networks.
The network layer has
two main functions. One is breaking up segments into network packets, and reassembling
the packets on the receiving end. The other is routing packets by discovering
the best path across a physical network. The network layer uses network
addresses (typically Internet Protocol addresses) to route packets to a
destination node.
5. LAYER
5: SESSION LAYER
The session layer
controls the conversations between different computers. A session or connection
between machines is set up, managed, and terminated at layer 5. It is
responsible for opening sessions, ensuring they remain open and functional
while data is being transferred, and closing them when communication ends. The
session layer can also set checkpoints during a data transfer—if the session is
interrupted, devices can resume data transfer from the last checkpoint.
6. LAYER
6: PRESENTATION LAYER
The presentation
layer formats or translates data for the application layer based on the syntax
or semantics that the application accepts. Because of this, it at times also
called the syntax layer. It defines how two devices should encode, encrypt, and
compress data so it is received correctly on the other end. The presentation
layer takes any data transmitted by the application layer and prepares it for
transmission over the session layer.
7. LAYER
7: APPLICATION LAYER
At this layer, both the end user and the application layer interact directly with the software application. It provides protocols that allow software to send and receive information and present meaningful data to users. The application layer identifies communication partners, resource availability, and synchronizes communication. A few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System (DNS).
WHY DOES OSI MODEL MATTER?
The open system interconnection model (OSI model) is a conceptual model that simplify the communication between two end points through layers or functions. The OSI model defines the network functions that occur at each layer. More essential, the OSI model enables an understanding of how data flows throughout a network.
source: https://hackonology.com/courses/computer-networking/lesson/osi-model/
The OSI reference model supplies a
number of benefits in understanding how network function by doing the
following:
Decreasing problems: the OSI model breaks
network communications into sections, simpler parts.
Assisting modular engineering: the OSI model allows
different types of network hardware and software to communicate with one
another.
Accelerating development: the OSI model
supplies for successful updates and improvements to individual parts without
affecting other parts or having to rewrite the entire protocol.
Easier teaching and learning: the OSI model breaks
network communications into smaller components to make learning easier.
Using communication: the OSI model helps
us to send a data through layers, starting from application layer and end the
physical layer.
HOW DATA FLOWS THROUGH THE OSI MODEL
A data to be sent
must travel to the seven layers of the OSI model on the sending device and then
up to the seven layers on the receiving side through a network.
An example of this is
when we want to send an email to someone. The email that will be sent will be
forwarded by the email sending application to the application layer which will
choose a protocol and forward the data to the presentation layer. Then the presentation
layer will compress the data and pass it to the session layer which will
initialize the communication session.
After initializing
the data communication session, the data will be forwarded to the transport
layer of the sender to be segmented. The data will be broken down into packets
at the network layer which will be further split into frames at the data link
layer. Then the frame will be sent by the link layer to the physical layer
which will convert the data into a bit stream of numbers 1 and 0 and send it
through the physical media, for example, a cable.
Once a stream of bits
enters the receiving device via a physical medium such as a WIFI, the data
flows through the same set of layers on the device, but in the opposite order.
First of all, the bit
stream data will be converted by the physical layer into frames and will be
passed to the data link layer. Then the data link layer will reattach the frame
into a packet for the network layer. Then the packet will be converted into
data by rearranging the segments generated by the network layer.
Then the data will flow to the session layer and pass it to the presentation layer and end the communication session. The presentation layer will uncompressing that data and pass it to the application layer. The application layer converts this data so that it can be read by humans and displays it on the screen of the receiving device.
SUBNETTING
CALCULATION
FSLM
192.168.10.0/26
|
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
|
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
|
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
|
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
|
25 |
26 |
|
|
|
|
|
|
|
Class |
4 Faculties |
Subnet Mask |
Host |
Subnet Block |
|
C |
4 subnets 256/4 = 64 IP address each faculty |
64 + 128 = 192 255.255.255.192 |
64 - 2 = 62 Hosts |
256 - 192 = 64 it will be 0, 64, 128, 192 |
CALCULATION for 4 SUBNETS
|
|
Subnet Address |
Host Address Range |
Broadcast Range |
|
1 |
192.168.10.0 |
192.168.10.1 – 192.168.10.62 |
192.168.10.63 |
|
2 |
192.168.10.64 |
192.168.10.65 – 192.168.10.126 |
192.168.10.127 |
|
3 |
192.168.10.128 |
192.168.10.129 – 192.168.10.190 |
192.168.10.191 |
|
4 |
192.168.10.192 |
192.168.10.193 – 192.168.10.254 |
192.168.10.225 |
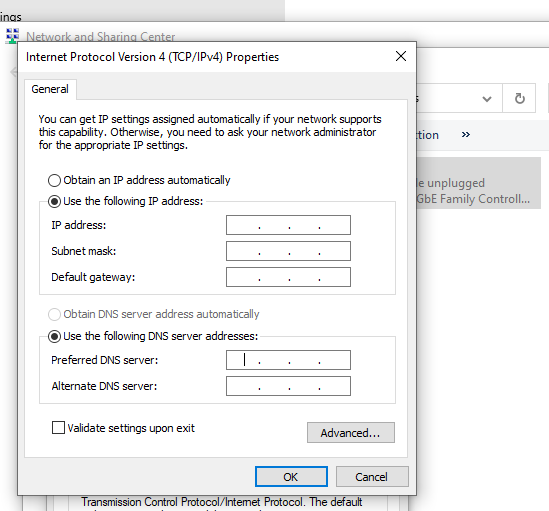
TCP/IP CONFIGURATION
The screenshots of how to
assign static IP address (TCP/IP)
- The first step we need to do is to open the
network adapter settings.
- Then right click on my network adapter
(Ethernet) and after that I’m going to click properties.
- Then inside properties I want to select
(internet protocol) version 4 TCP/IP version and I’m going to click
properties.
- This step you have to click (use the following
IP address) and you need to use IP address, subnet mask, default and DNS
sever.
- If we want to use IP address, we have to press
the windows key and the letter R and then we are going to type CMD and
press ENTER.
- When terminal opened, we are going to do IP
configuration box (first picture) and then press ENTER and this is going
to give me quite a few information (second picture).
- Now, we need to complete the IP address from
terminal to the IP address but we have to change the last decimal numbers
of IP address.
- This section we are going to add the subnet
mask, default gateway and DNS sever.
- This is the last step we will click (close)
and then we will finish our TCP/IP configuration.
***************** That’s all from us Group 9 thank you *****************












Komentar
Posting Komentar